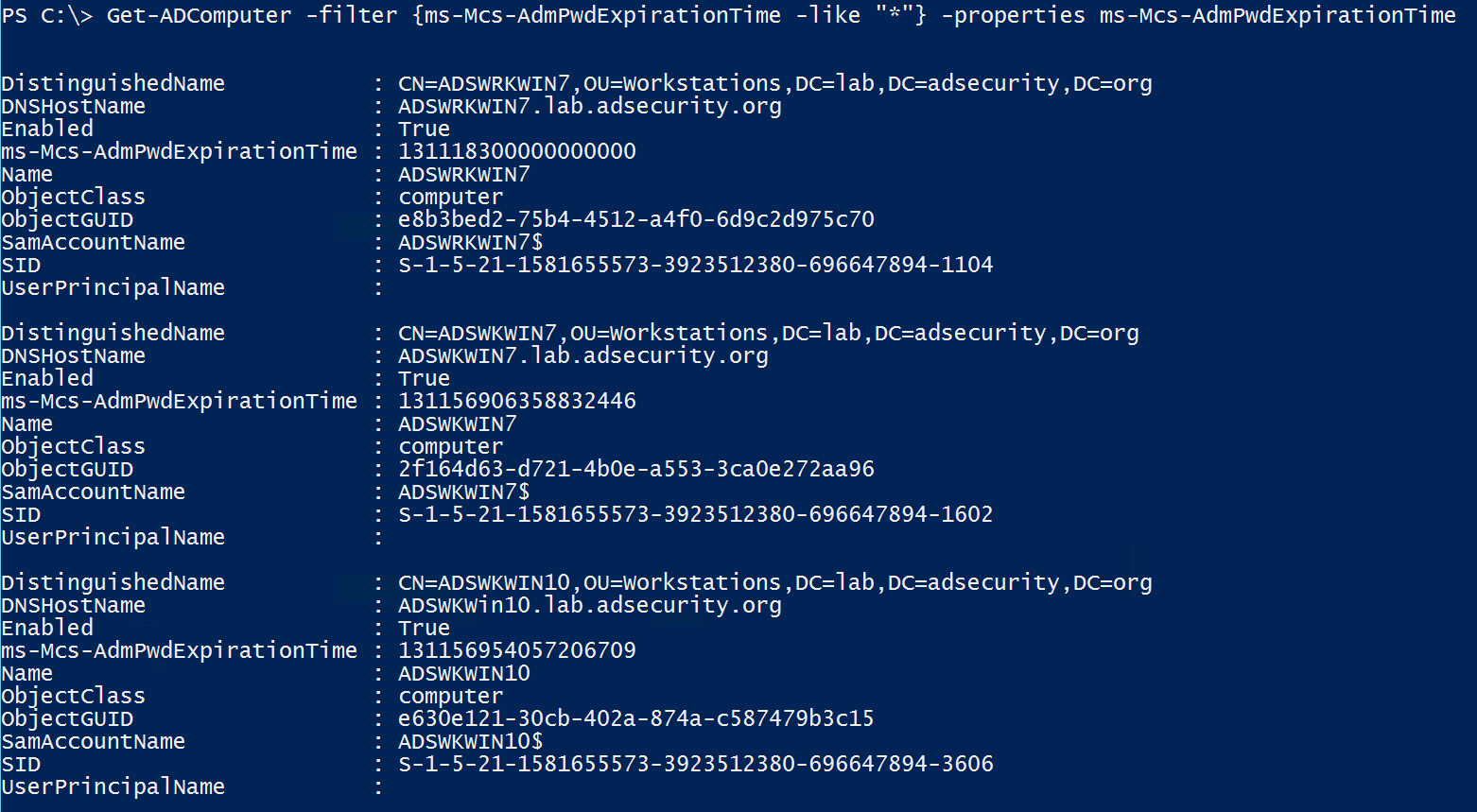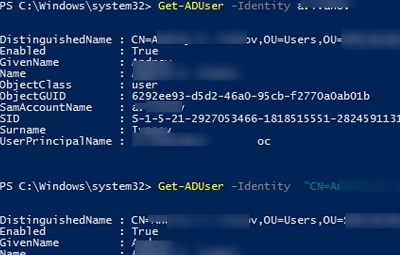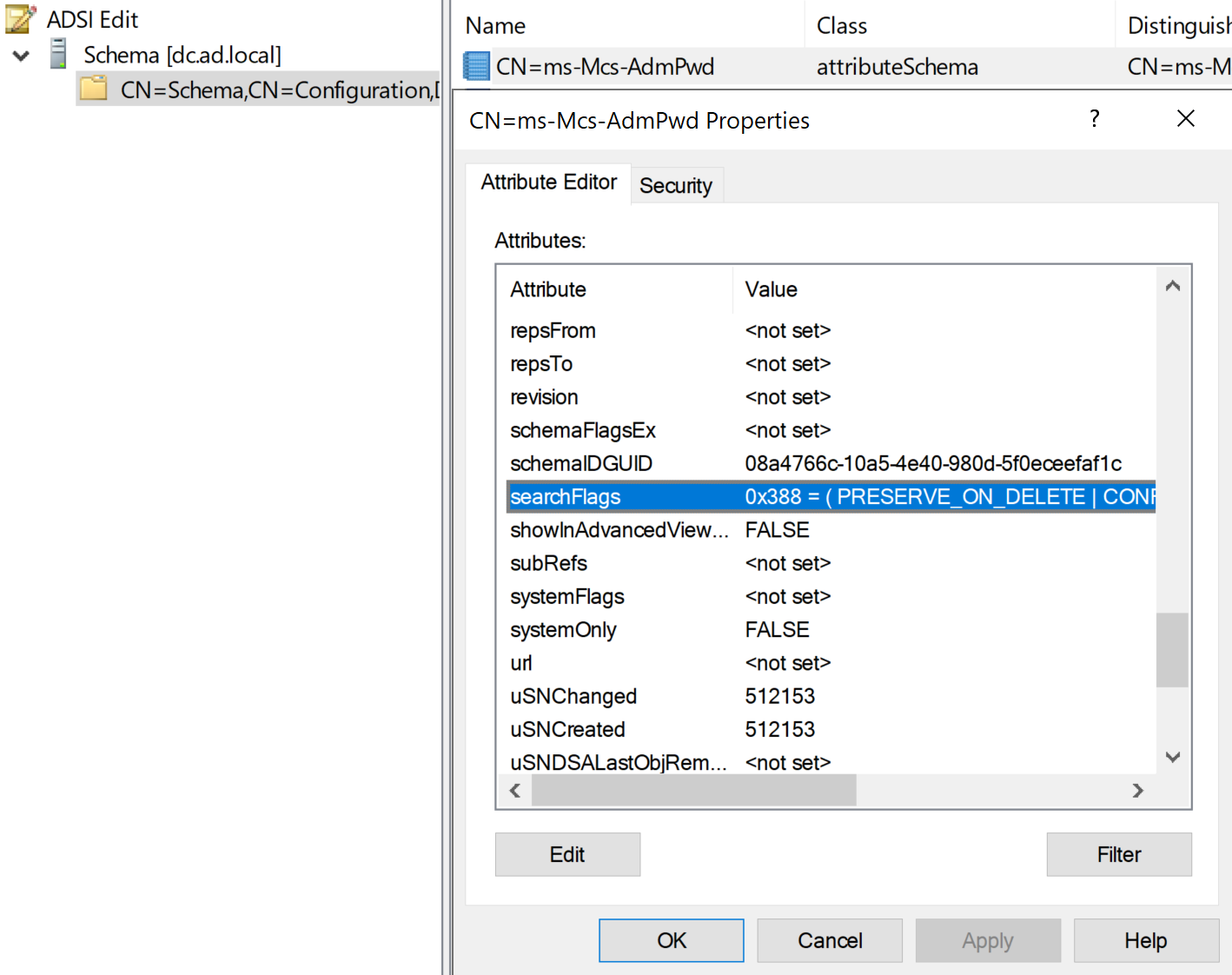
DirSync: Leveraging Replication Get-Changes and Get-Changes-In-Filtered-Set | simondotsh's infosec blog

How to Secure Confidential Attributes with Active Roles -Script Provided - Active Directory Management (AD Mgmt) - Blogs - One Identity Community
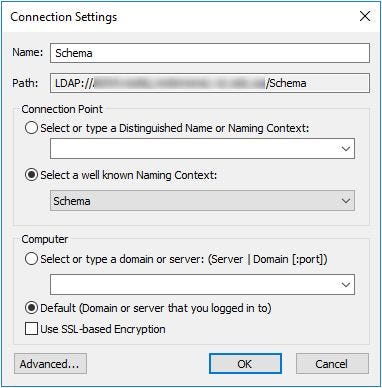
Easily configure confidential attributes in Active Directory | by Sam Neal | Beyond the Helpdesk | Medium

LDAPFragger: Bypassing network restrictions using LDAP attributes | NCC Group Research Blog | Making the world safer and more secure

How to scale your authorization needs by using attribute-based access control with S3 | AWS Security Blog
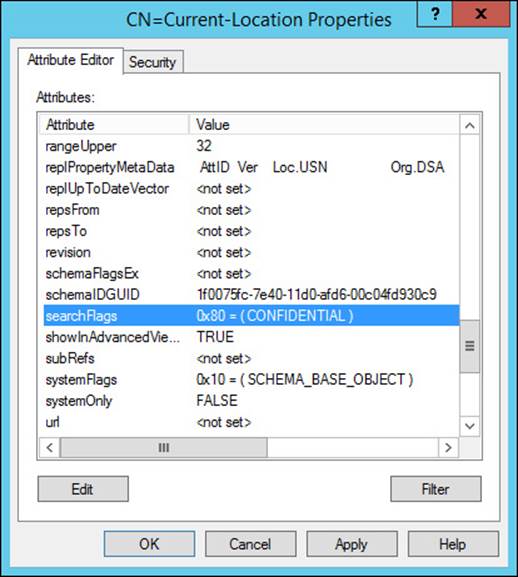
Design and implement an Active Directory infrastructure (physical) - Exam Ref 70-413 Designing and Implementing a Server Infrastructure, Second Edition (2014)

Using the Confidentiality Bit to Hide Data in Active Directory | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More

Protección de Active Directory - 10 Securing Active Directory From a business perspective, Active - Studocu
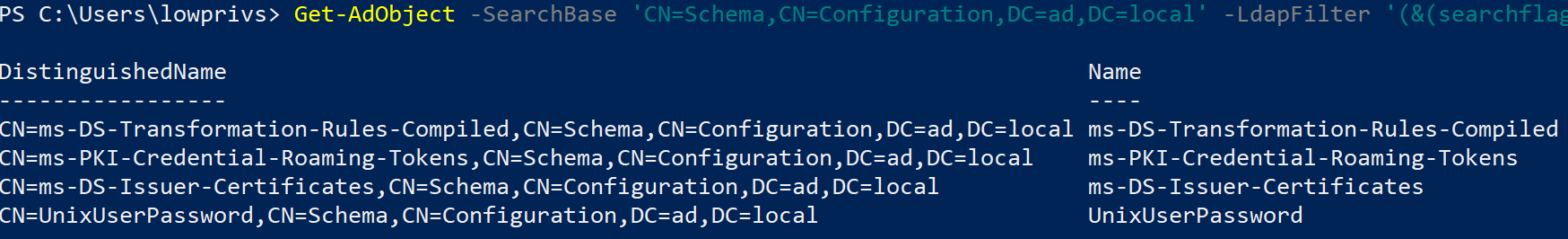

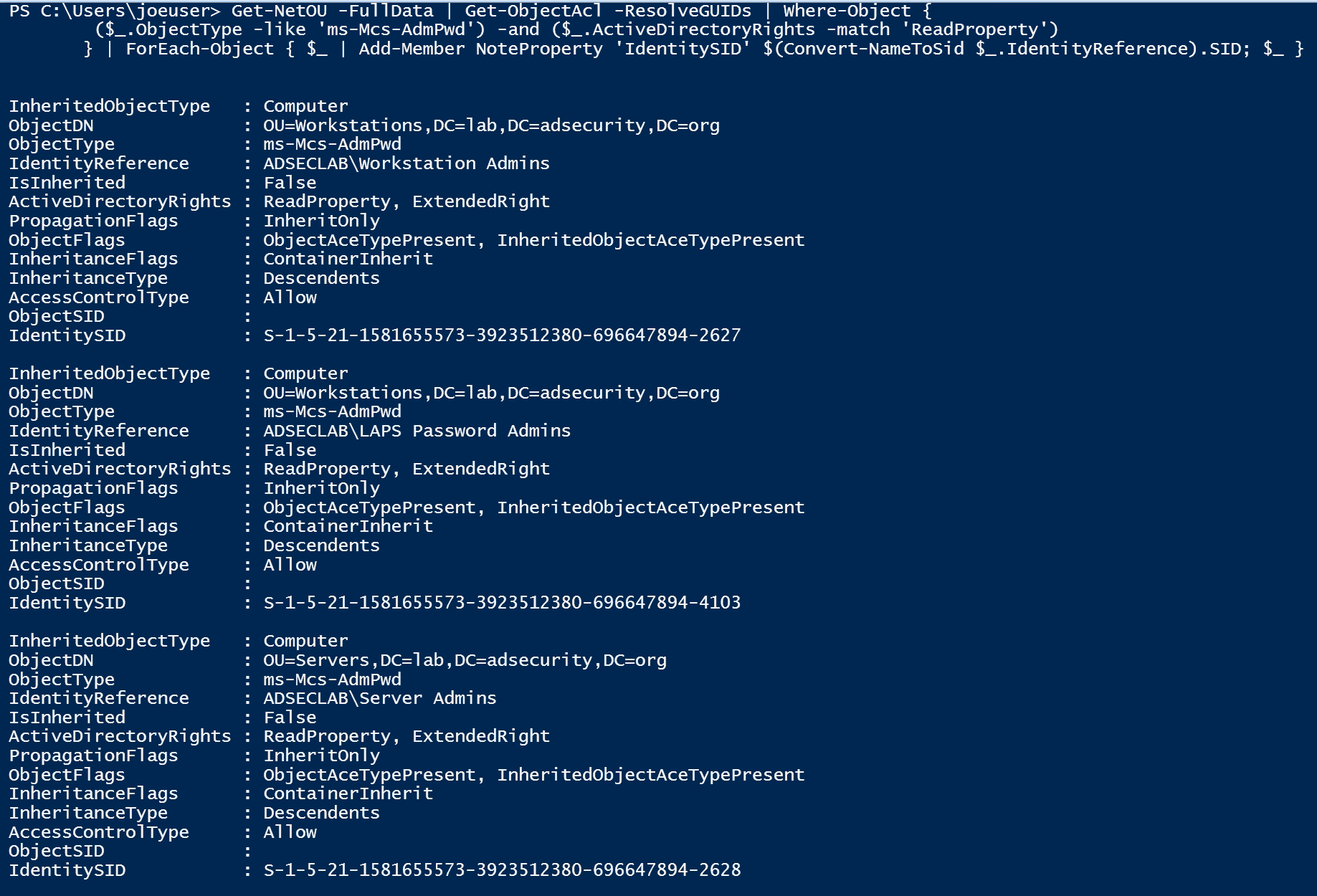




![4. Active Directory Schema - Active Directory, 4th Edition [Book] 4. Active Directory Schema - Active Directory, 4th Edition [Book]](https://www.oreilly.com/api/v2/epubs/9780596155179/files/httpatomoreillycomsourceoreillyimages225067.png.jpg)
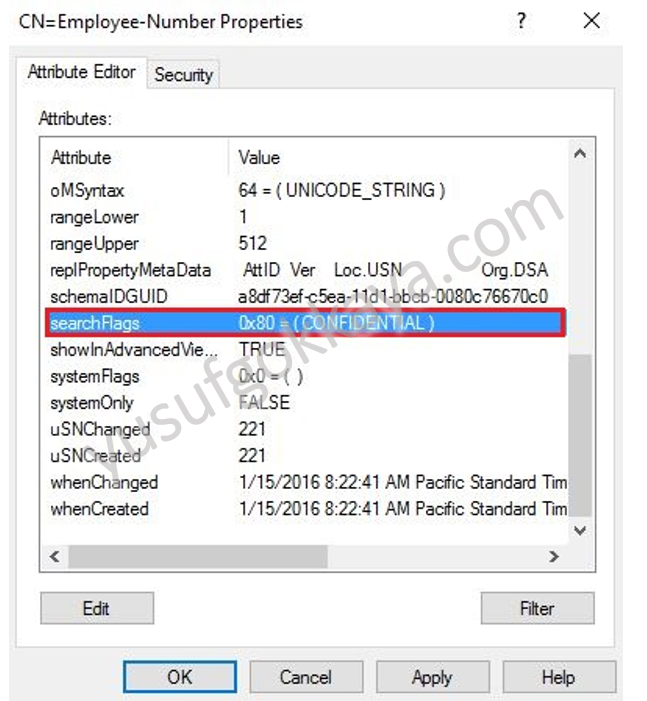
![SOLVED] Making an AD Attribute Confidential SOLVED] Making an AD Attribute Confidential](https://content.spiceworksstatic.com/service.community/p/post_images/0000319728/5b5f09dc/attached_image/Capture.jpg)
![SOLVED] Making an AD Attribute Confidential SOLVED] Making an AD Attribute Confidential](https://content.spiceworksstatic.com/service.community/p/post_images/0000320071/5b60d409/attached_image/2018-07-31_14-26-22.png)