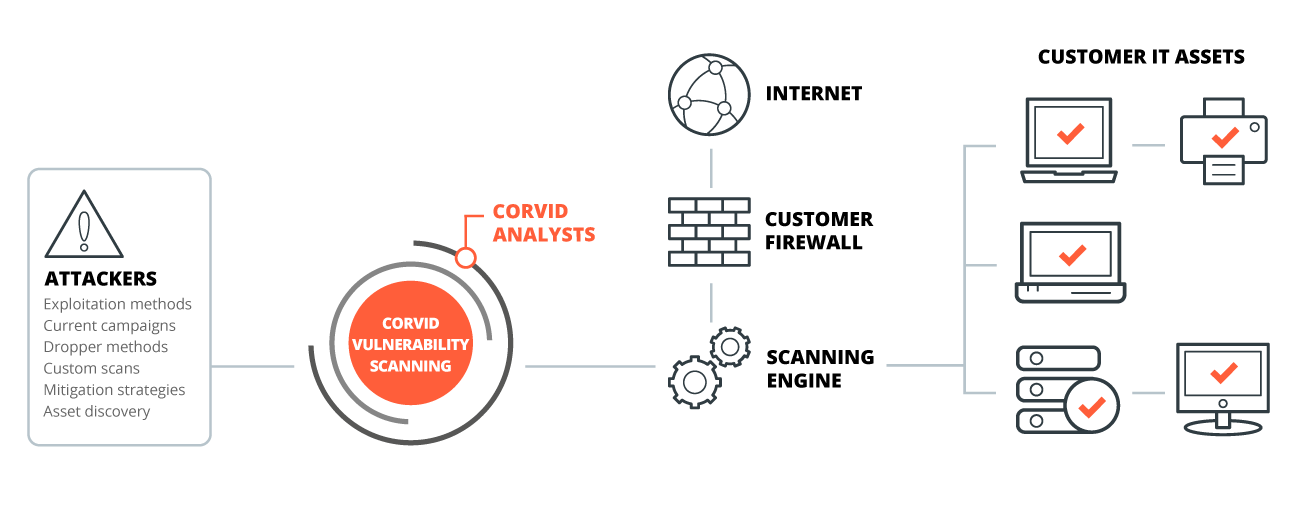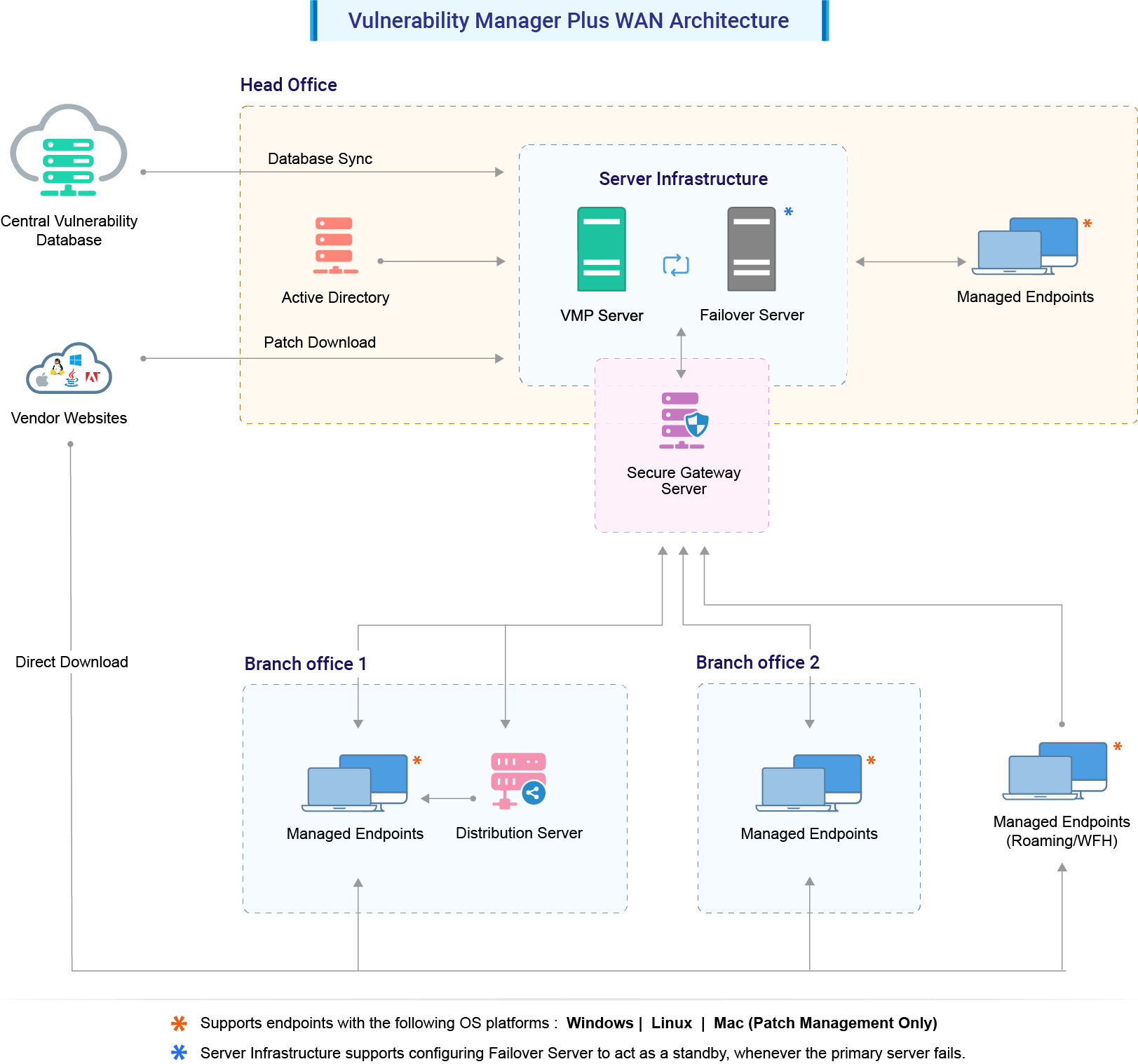
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus
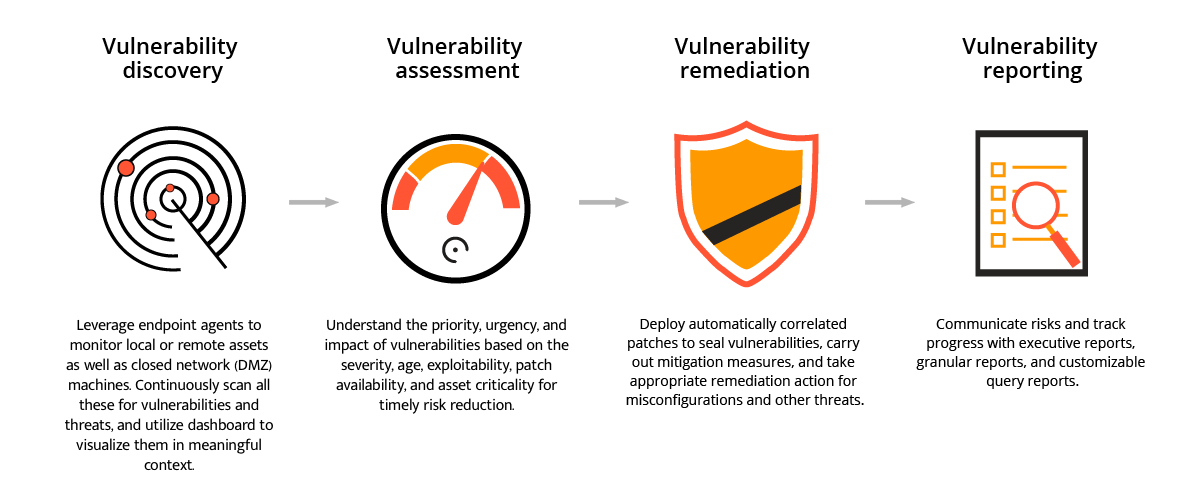
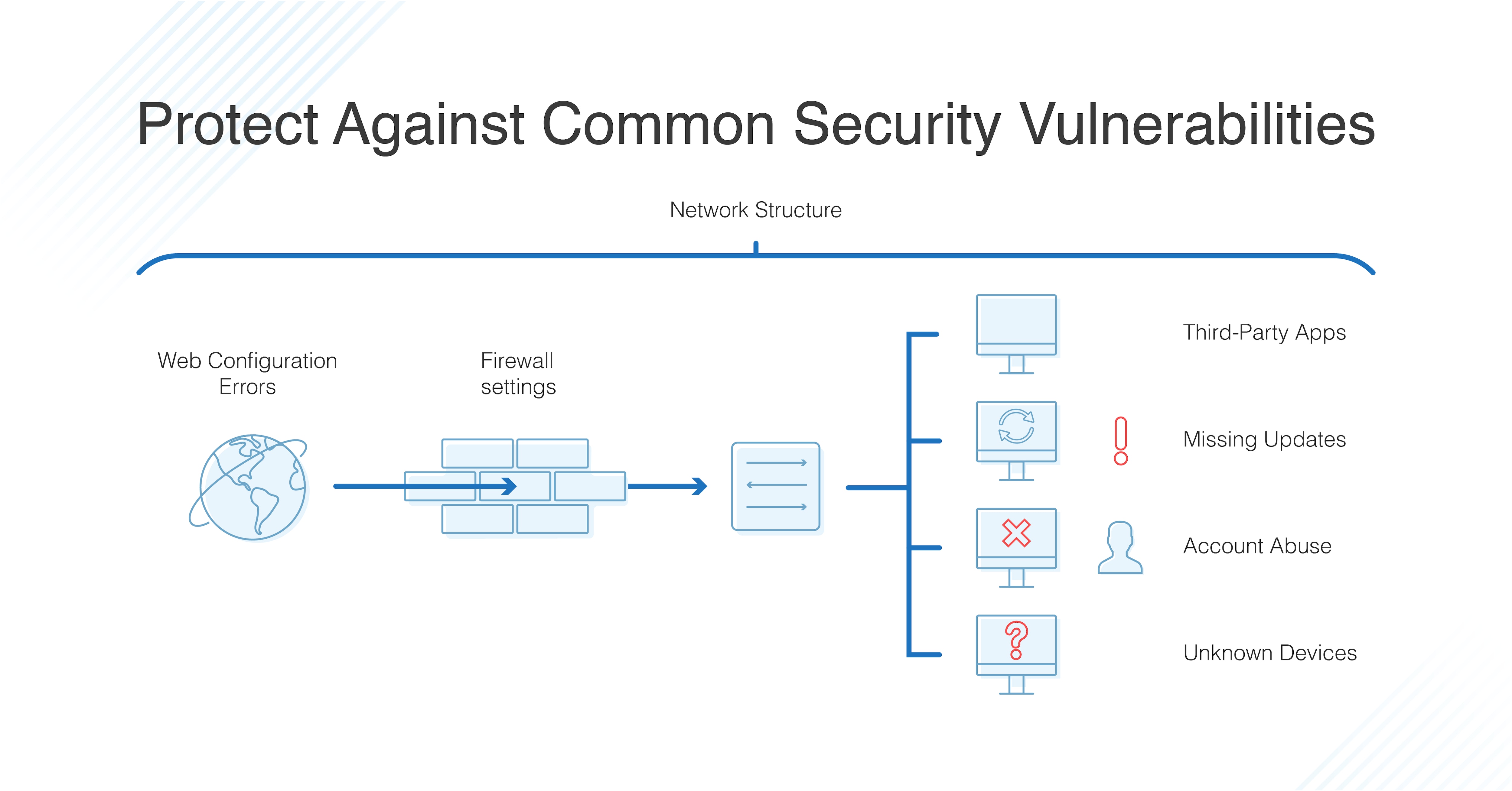
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus

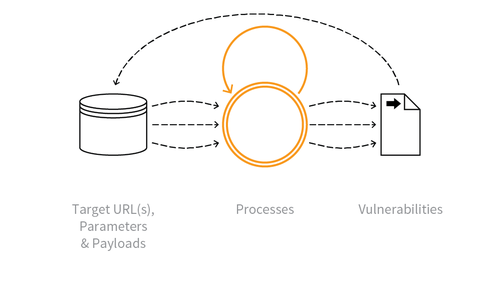
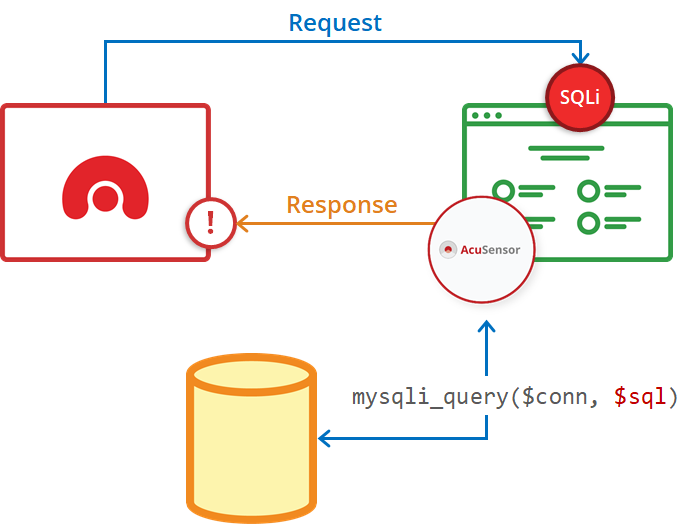
How the Network Vulnerability Scanner works using Nuclei, the new scanning detection engine : r/pentest_tools_com
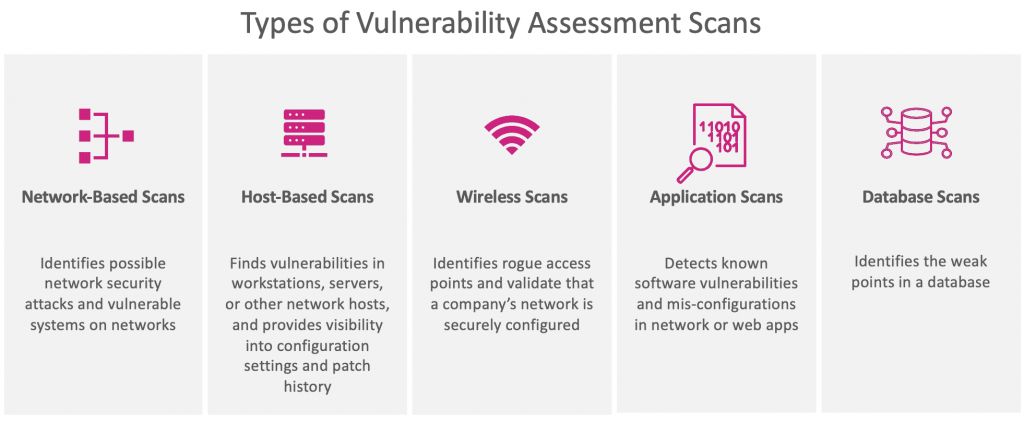
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus
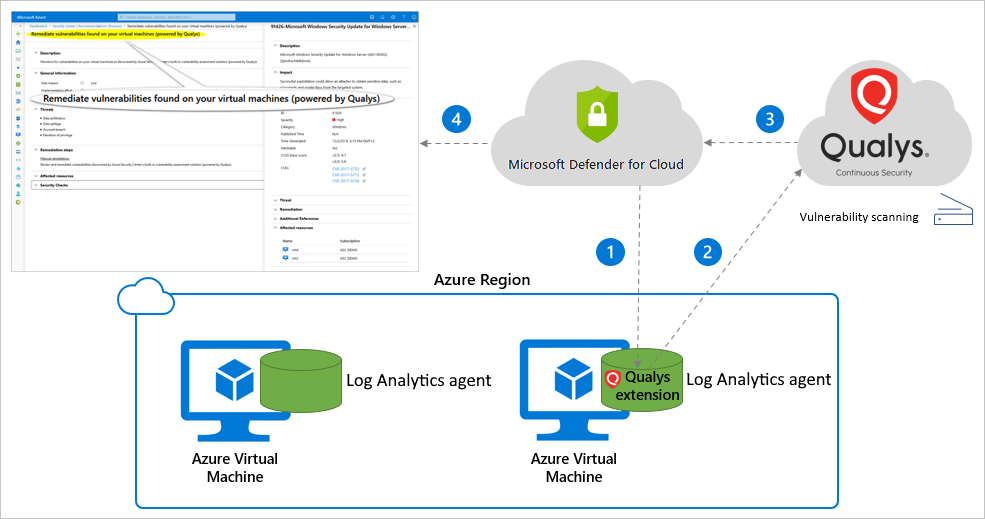
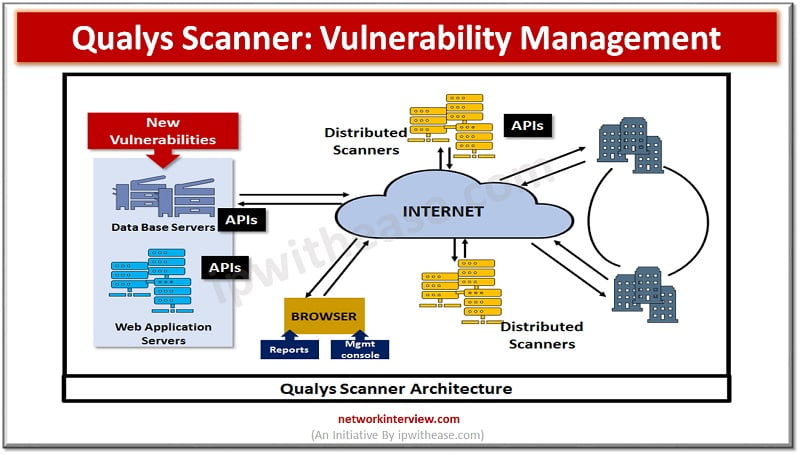
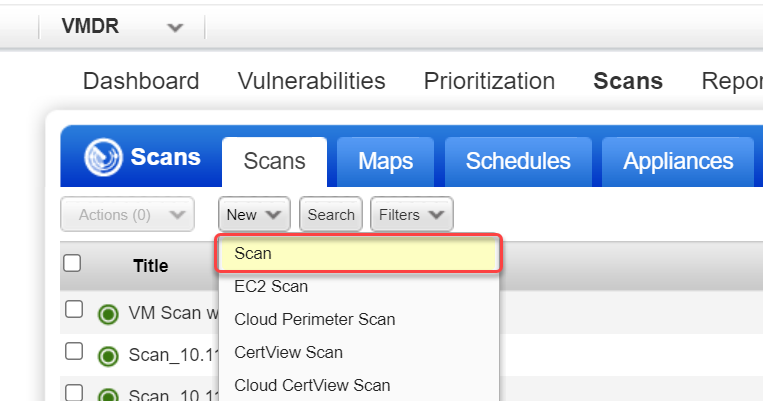
Enable vulnerability scanning with the integrated Qualys scanner - Microsoft Defender for Cloud | Microsoft Learn